Think about all the data your organization generates, uses, and stores. Things like customer contact information, product specs, financials, inventories, policies, or communications. That’s a lot of moving parts. Do you have a data compliance policy in place to protect it all?
Estimates predict that in 2025, the world will create and replicate 163 ZB of data, representing a tenfold increase from the amount of data created in 2016.
Source: IDC
Just a little perspective on that IDC prediction: A zettabyte (ZB) has a capacity of 10 bytes to the 21st power. That’s one billion terabytes (or, an astonishing trillion gigabytes).
Maybe you’re thinking, “Wow—we need more cloud storage for all that data.” But before you click the purchase button, ask yourselves a few questions about managing your data.
- What happens if your org’s confidential data are accidentally shared by a user?
- Do employees know which data are okay to share—and with whom?
- How long should you keep digital communications in case of lawsuits or litigation?
- If you need to access critical files four years from now, how will you find those files?
The answers to these questions are critical to the creation of your data compliance policy.
So let's review. Exactly what is data compliance?
Put simply, data compliance refers to regulations that protect sensitive data. More specifically, compliance practices dictate how data is organized, stored, and shared.
Think of it this way. As someone in charge of security, you likely spend the bulk of your time preventing cybersecurity breaches from the outside. Compliance represents the other side of the coin—security from the inside out. Which means your end users also must understand their role in compliance.
80% of corporate data is "dark"—unclassified, unprotected, or ungoverned.
Source: Microsoft
With all that dark data, compliance is a critical issue. But for whom?
Case in point: some security executives think that compliance falls outside a typical CISO’s role. However, the role of the CISO is evolving.
Understand the 6 types of security executives
According to a Forrester report, The Future of the CISO, (available to Forrester subscribers or for purchase) there are six basic types of CISOs.
Unsurprisingly, your type might be a mix, and it can change. It’s also possible that your organization might need you to wear more than one of these CISO hats.
- Transformational CISO – Leads an organization through a cybersecurity change effort. Creates and implements a strategic plan to transform the organization. Keeps customers and business outcomes at the focus of the plan.
- Postbreach CISO – Works to resolve any outstanding problems after a major breach. Focuses on improving cybersecurity to prevent future breaches. Understands that it may be a long process until the breach is fully resolved.
- Tactical/operational CISO - Sorts out operational and technical issues in an organization. Creates an action-oriented, tactical team. Thinks of security in operational terms.
- Compliance/risk guru – Treats security as a risk management conversation. Considers compliance issues a top risk to the organization. Prefers to work in a disciplined, detail-oriented process.
- Steady-state CISO - Maintains cybersecurity program, neither transforming nor reducing current security posture. Since technology doesn’t sit still, this role focuses on consistent, steady improvement—without rocking the boat.
- Customer-facing evangelist - Takes charge of security for the organization, its products and services that generate revenue. This role is the face of cybersecurity to customers and investors. Values security, ethics, and customer trust as keys of success.
Source: Forrester
The truth is, no matter what type of CISO you are, you need to be aware of protecting your data from the inside out. Not just threats that come from outside the company.
Of all the types of CISOs, the compliance/risk gurus are not usually common. But as we just said, compliance and end-user security behaviors are important to all CISO types.
Unfortunately, 88% of organizations no longer have confidence to detect and prevent loss of sensitive data.
Source: Microsoft
As most CISOs focus on the physical and virtual security of their organizations, they may have less time to deal with the human element of compliance; namely, the end users in their organization.
95% of cybersecurity breaches are due to human error.
Source: Cybintsolutions
If this situation feels familiar, there’s a way to scale your efforts and help your entire organization be more compliant with data that gets accessed and shared every day.
Meet with a data compliance committee
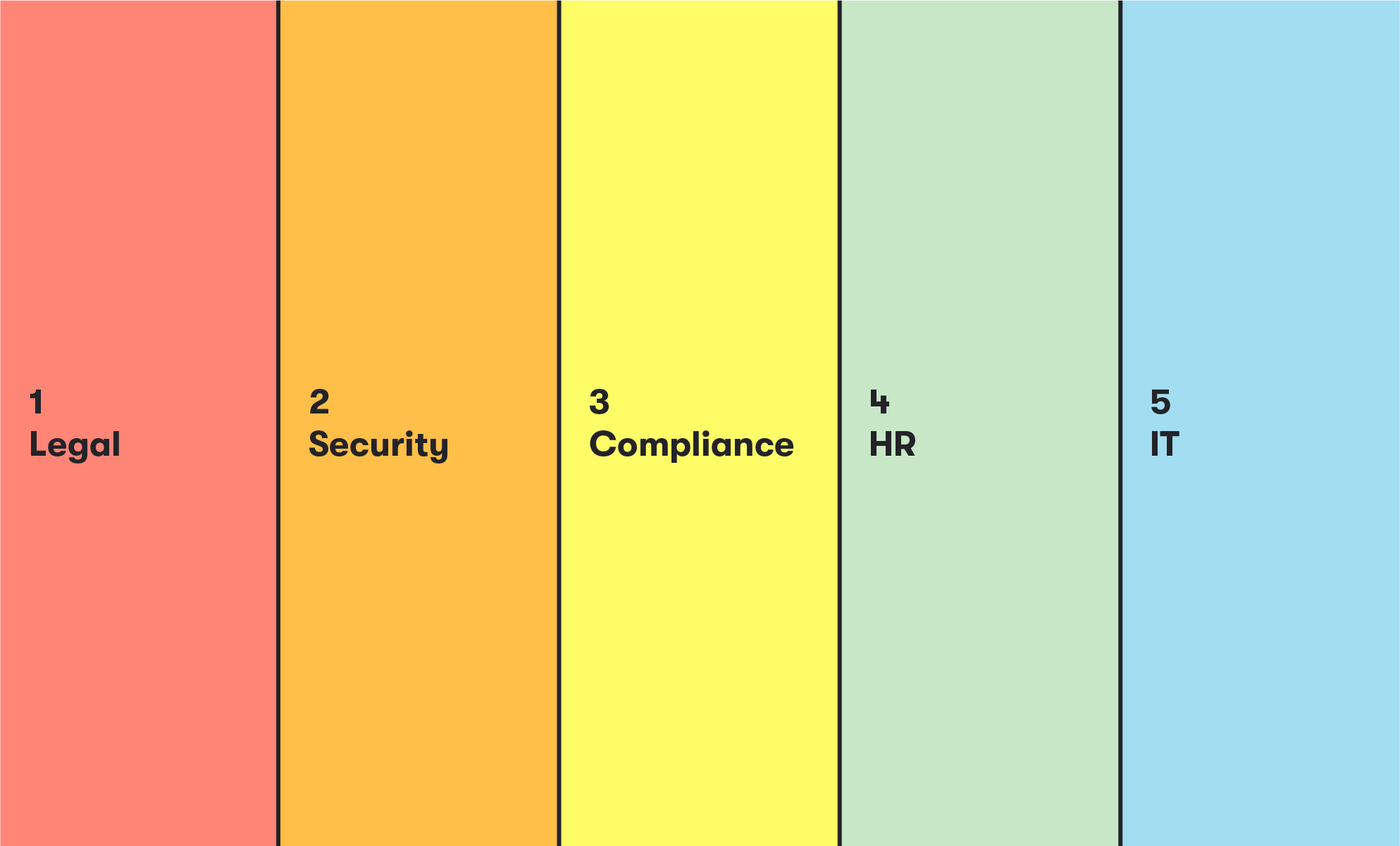
To get going on your compliance policy, expand your discussion to include leaders, decision makers, and policy implementers in legal, security, compliance, human resources, and IT.
Feel like there’s no time? Remember, no matter how tempting it is to kick the can down the road, your organization can’t afford to pay the costs of non-compliance.
83% of companies are experiencing challenges in ensuring regulatory and industry compliance from ineffective data management.
Source: InteliSecure
Ideally as CISO, you can bring multiple teams together so everyone understands the legal and regulatory needs of your organization. Together, you will create specific policies around security, compliance, collaboration, and productivity tools.
As you break down the legal and regulatory needs of your organization, focus on:
- Data protection
- Sensitivity
- Loss prevention
- Governance
- eDiscovery
If you work in healthcare, you’ll also deal with HIPAA and PII requirements. Financial services will have different requirements around PII, and government agencies will additionally focus on freedom of information and public disclosure.
Depending on your industry, discuss an approach that’s best for your organization’s needs. To start, familiarize your group with a relevant compliance tool.
For instance, if your org holds E5 licenses for Microsoft 365, visit the Microsoft 365 Compliance Center. Or, if you have a premium or enterprise license for Google Workspace for Business, explore Google Vault.
Build your users' compliance skills
Next, consider how you will help end users be more compliant via:
Education—discuss best practices, share compliance policies, build technology skills, and regularly poll users about their security awareness.
Repetition – to increase awareness, continually reinforce the principles shared during training.
Follow-up—ensure completion of assigned training, track behavioral change, and regularly communicate updates or policy revisions.
No doubt you’re busy maintaining security defenses, such as multi-factor authentication, encryption, firewalls, VPNs, vulnerability scanners, and so on. Most days, your to-do list seems endless.
When it comes to training end-users in compliance and security, does this sound like you?
- I don’t even think about my end-users.
- The users will mess everything up.
- They will create more security risks.
- I don’t have time for this.
- Isn’t end-user training the job of IT and HR?
Just remember, the more compliant users are in their technology skills and habits, the better they can help protect data from the inside out, especially as they change their behavior around their software.
Of course, the trick is getting your end users to apply the information you share.
For instance, what are your data retention policies around Microsoft Teams and Outlook? If needed, could you offer evidence that your users are following compliance best practices around these tools?
Start with user education, repetition, correction, and follow-up as mentioned above. And monitor user activity in Microsoft 365 or Google Workspace, so you’ll know which data to retain (and for how long).
Over time, measure user progress toward compliant behavior. Keep a careful record of end-user training and the trends that result.
If you don’t know where to start, let BrainStorm walk through the process with you.
Take baby steps toward compliance
Teaching your users to correctly and safely use your organization’s security, compliance, collaboration, and productivity tools is a daunting task. That's one reason why you need to work with IT, HR, and other departments to effectively scale your efforts.
Also, realize that any start on compliance is better than no effort at all.
At BrainStorm, we find that annual security awareness training isn’t the most effective way to go about compliance training. Instead, it’s far more effective to share ongoing information in small doses.
What could this look like? Picture a series of short, manageable skill-building events, videos, and live trainings that offer steady reinforcement. Include polling and opportunities for user feedback.
To help jumpstart user compliance and shore up users' security awareness more than once a year, download The Ultimate Guide to Security Awareness Training.


